Manual Vs Automated Pentesting: Why you should treat your security like your car
Annual pen-tests still have their place and are extremely important to many customers for compliance reasons, however automated pentesting can offer even more benefits.
Manual Pen-testing Vs Autonomous Pen-Testing
Manual pen-tests are run over the course of a few days once a year and potentially result in a big list of issues to fix that were found during these few days, the report of vulnerabilities and infrastructure issues that require attention can vary depending on how thorough the consultant running them has been. Of course, annual pen-tests still have their place and are extremely important to many customers for compliance reasons, however they are expensive and are most useful to get a certificate of completion for insurance or compliance reasons.

To visualize it all let’s look at the similarities between annual pen-tests and a car MOT. You take your car in and leave it to be tested, it’s one of the most expensive annual occurrences with owning a car, the garage gives you a list of things that need fixing which costs you more time and money before you can get your certificate to go about your daily business.

A couple of weeks later there’s a an engine management fault costing more time and money to fix, a month later you spot a patch of oil under the car, if left this will cause further damage to the engine, more time and money to fix but will hopefully prevent bigger issues and so the battle with keeping an older car on the road continues…..
You could view annual pen-tests in a similar way, a quick but expensive exercise to gain a certificate, but even over the course of a few days testing it is impossible to predict what will happen in the 11-12 months between tests. Ask yourself these questions also, how thorough were the tests, are they running the same tests every year, have we covered the latest vulnerabilities, what was missed during these tests, have there been any zero-day exploits since my pen-test?

Autonomous pen-testing on the other hand gives us the ability to continuously test your entire infrastructure or specific segments of it for the latest vulnerabilities and produce a prioritized list of the most important things to fix. These tests can be scheduled to run daily, weekly, monthly or ad hoc as required for example when a new CVE is discovered, or new machines are added to the network. We can look at the results over time and see a graphical representation of how the remediation steps are affecting cyber resilience metrics as you implement fixes.

Flexibility
Tests can be run on internal infrastructure, external assets or in the cloud across many subnets. Where there are multiple geographical locations, this is not a problem just connect a VM at each location to run the tests. These can be run when you like, on-demand or scheduled.
What can I run a test against?
There are a huge number of tests that can be run as required or on a scheduled basis, see below:

The proof is in the pudding
Nothing is hidden all vulnerabilities that were exploited are clearly listed out with the proof to show how compromise was achieved.
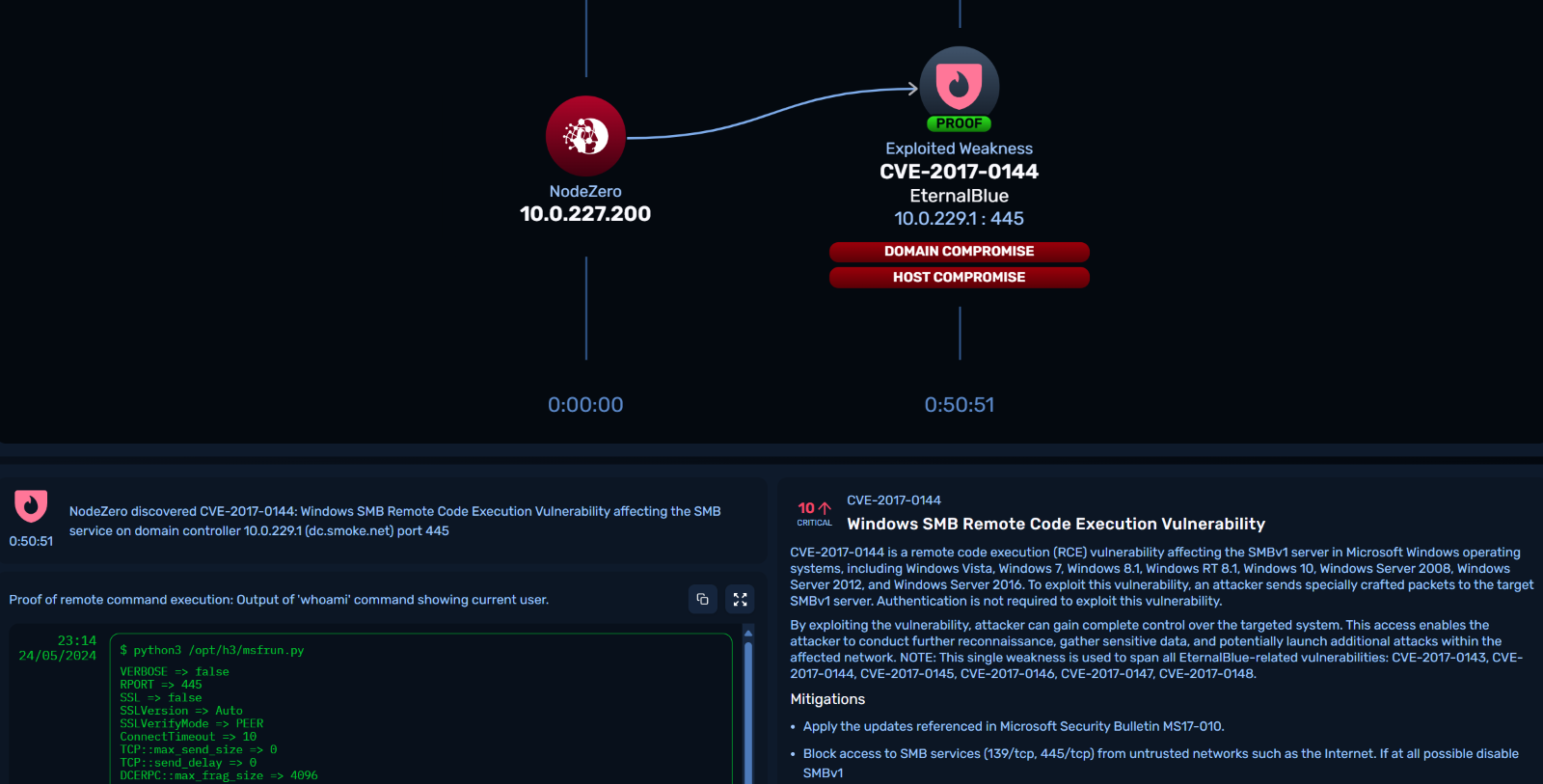
Find fix and verify
Once a pen-test has completed and you have worked on the list of priority Impacts and Weaknesses, you will want to know if your hard work is paying off. One way to do this is wait for the next full pen-test and look at the results, however, these can take a while especially in large organisations and it would be nice if you can tick your homework as you go. This is where 1-click verify comes in, some of the vulnerabilities found can be added to a shopping cart and a quick pen-test run just on these to see if your infrastructure is still affected. This is a super quick way to see how your efforts to remediate issues are progressing.

Rapid Response
These are again super-fast tests against the latest N-day vulnerabilities, these are constantly updated and designed to help you quickly deal with the latest exploits before an attacker takes advantage should you be susceptible to it.

Tripwires
These go a step further than just showing you exploits and vulnerabilities. Tripwires are suggested in your pen-test reports and can be deployed as decoys within your environment, these look like legitimate files or credentials and should an attacker sniffing around your network stumble upon one you will be notified immediately.

The reports produced from Autonomous pen testing are invaluable, giving a clear action plan, and remediation steps.



Conclusion
Yes, as you can probably tell I am a big fan of Autonomous pen-testing and hopefully you can see why and the importance / benefits of this from the info in this blog post. Manual pen-tests still have their place but are limited by time frames and scope of testing, running autonomous tests will expose any gaps you may have using the latest techniques and up to date CVE’s along with remediation steps and a clear timeline of your resilience to cyber risks as you deal with them.
Cyber Vigilance have our own Managed Autonomous Pen-testing Service powered by NodeZero®, and all the screenshots in this document were taken from this fantastic platform. Please get in touch with us any time if you would like a discussion around this, a demo or any more info always here to help.

Chris Faulkner
Senior Cyber Security Consultant
Get safer now
See how Managed Threat Detection can make a difference for you. No obligation free trial.
©2025 Cyber Vigilance
Powered by Disruptive
Naggs Stable, Old Portsmouth Road, Guildford, Surrey, England, GU3 1LP